If you are new to the concept of zero trust in cybersecurity, it is fascinating to learn about its importance in protecting data. Zero trust involves making access decisions in the face of an untrusted network, meaning every user and device must be authenticated and authorized every time they access a resource.
At a workshop I recently attended, the presenter covered the private sector and government’s perspective on zero trust and its evolution over the years, the challenges of making the inside of a network untrustable, and how technology has evolved to address this issue.
Many organizations describe zero trust differently, leading to confusion. However, the government has recognized its importance, defined it, and recently promoted its adoption. The Cybersecurity & Infrastructure Security Agency strategy released in March references zero trust, and there are various methodologies for implementing it, such as the CISA maturity model or NIST’s architecture.
The NIST definition of Zero Trust “provides a collection of concepts and ideas designed to minimize uncertainty in enforcing accurate, least privilege per-request access decisions in information systems and services in the face of a network viewed as compromised.” Page 4 NIST SP 800-207
Meanwhile, CISA has developed an architecture to assess and improve your company’s zero trust maturity. Their foundation includes five pillars: identity, device, network/endpoints, applications workload, and data security. Governance is at the bottom of their foundation because we need policies tying back to the policy to justify the controls to enforce the policies and understand why the rules are in place.
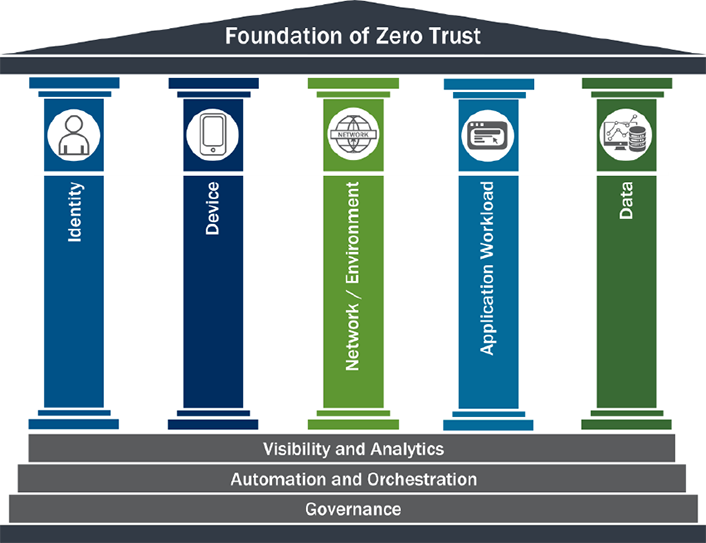
The presenter then described four approaches to zero trust security: Domain, Technology, Strategy, and Use Case Centric. The presenter recommended using multiple methods and creating a governance plan as the groundwork for our organizations. The presenter was from CDW and recommended updating our security policies and standards to achieve optimal maturity levels in implementing zero trust across all five pillars. They also mentioned it is essential to consider governance and administration, identity, privileged access management, and cloud security tools. Governance plays a significant role in defining policies and controls for cloud infrastructure. Practical steps such as using closed ecosystems, two-factor authentication, and air-gapped backups can help achieve zero trust in data backup.
To help organizations assess their current security maturity and develop a plan to improve their security posture, CDW offers services that focus on access management and other relevant skills and tools. Their services include a zero trust maturity assessment and a workshop to discuss concepts and determine the organization’s current level of maturity and desired outcomes based on the CISA maturity model.
In conclusion, the presentation informed me that zero trust is a critical concept in cybersecurity that involves making access decisions in the face of an untrusted network. Organizations can achieve optimal maturity levels in implementing zero trust across all five pillars by implementing updated security policies and standards and using cloud security tools and practices. CDW offers services to help organizations assess their current security maturity and develop a plan to improve their security posture, ensuring their data is protected against threats.